Module 8: Anonymity and Privacy in Cryptocurrencies: How to Keep Your Transactions Private
Introduction: The Myth of Cryptocurrency Anonymity
"Cryptocurrencies are anonymous" — one of the most widespread misconceptions that can cost you dearly. The reality is quite the opposite: Bitcoin and most cryptocurrencies are pseudonymous, not anonymous, and every transaction you make is permanently recorded on a public blockchain accessible to everyone.
Imagine: every purchase, transfer, and investment you make — all visible to anyone who knows your address. How much money you have, where you spend it, who you interact with. It's like having your bank statement published online with your name attached.
According to Chainalysis, over 95% of Bitcoin transactions can be linked to real identities given sufficient resources. Law enforcement agencies, tax authorities, and even private companies actively use blockchain analytics for deanonymization.
Critical to understand: Lack of privacy isn't just about "having nothing to hide." It's about security (targeted attacks on wealthy holders), freedom (financial surveillance), and basic human rights (the right to privacy).
In this lesson, you'll learn how deanonymization works, what privacy protection tools exist, and how to use them legally and safely.
Pseudonymity vs Anonymity: What's the Difference
What is Pseudonymity
Bitcoin and most cryptocurrencies are pseudonymous. This means:
- You use an address instead of your name (e.g., 1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa)
- The address isn't directly linked to your identity
- BUT all transactions from this address are public and traceable
- If the address is linked to your identity even once — your entire history is compromised
Analogy: Pseudonymity is like wearing a mask in a public place with cameras. The mask hides your face, but all your actions are recorded. If you take off the mask even once — your entire history can be reconstructed.
What is True Anonymity
True anonymity means:
- Impossible to link a transaction to an identity
- Impossible to trace the flow of funds
- Even knowing one point, the history cannot be reconstructed
- Metadata is hidden (IP addresses, timestamps, patterns)
Examples of true anonymity: Monero, Zcash (with shielded transactions), physical cash.
| Characteristic | Pseudonymity (Bitcoin) | Anonymity (Monero) |
|---|---|---|
| Addresses visible | ✅ Yes, all public | ❌ Hidden (stealth addresses) |
| Amounts visible | ✅ Yes, exactly | ❌ Hidden (confidential transactions) |
| Flow tracking | ✅ Fully possible | ❌ Impossible (ring signatures) |
| IP tracking | ⚠️ Possible without VPN | ⚠️ Possible without Tor/VPN |
| Identity linkage | ⚠️ Through KYC exchanges | ⚠️ Through KYC exchanges |
| Metadata | ✅ Public (time, gas) | ❌ Minimized |
How You Get Deanonymized: Methods and Techniques
Method 1: KYC on Exchanges (Most Common)
Most users compromise their privacy the moment they enter crypto through centralized exchanges.
How it works:
- Register on Binance/Coinbase → complete KYC (passport, selfie)
- Buy BTC → withdraw to your wallet
- The exchange knows: name, address, bank account, wallet address, purchase amount
- All transactions from this address are now linked to you
- The exchange is required to share data with tax authorities and law enforcement
Scale of the problem:
- Coinbase shared data on 13,000 users with the IRS (2017)
- Binance shares data with more than 40 law enforcement agencies
- EU requires all exchanges to report under MiCA regulation
- Travel Rule requires information sharing between exchanges for transfers >$1000
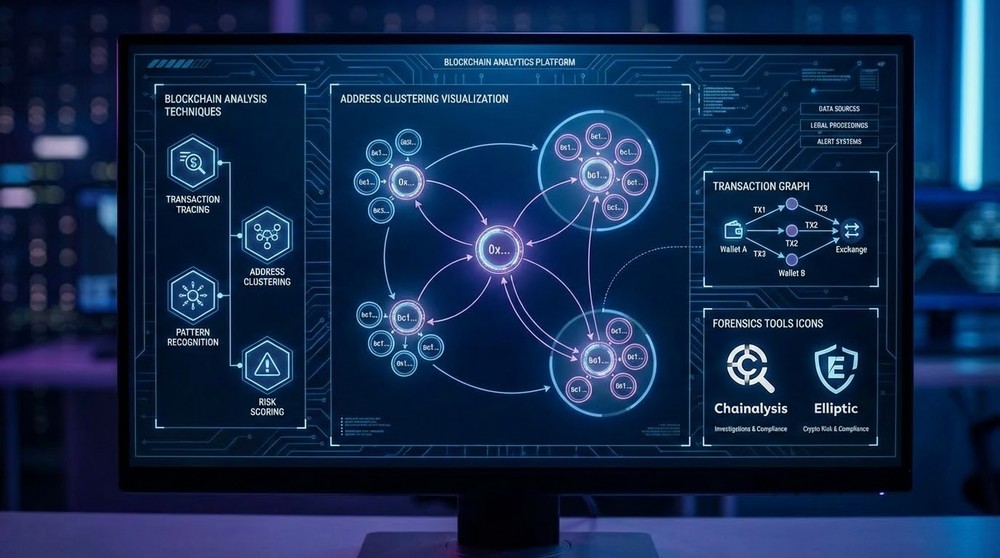
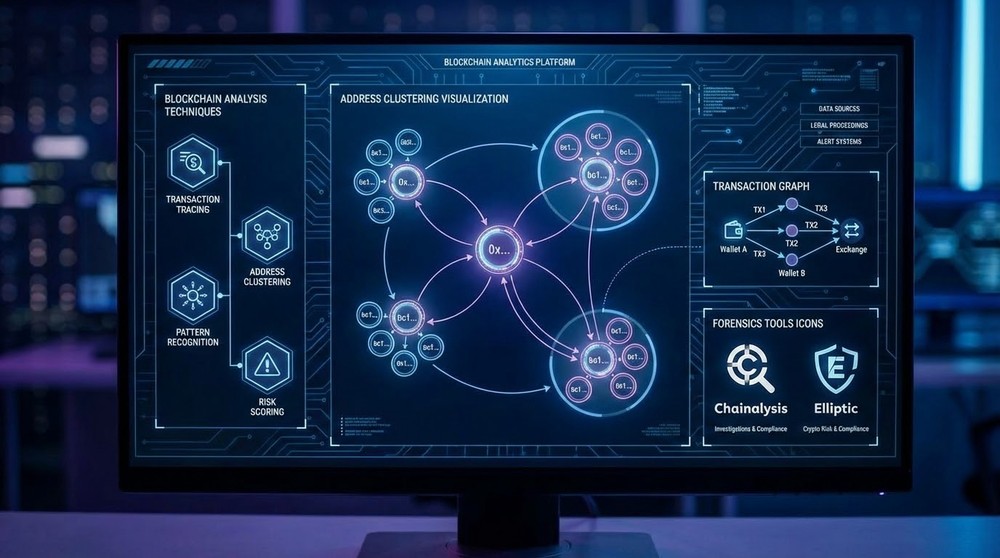
Method 2: Blockchain Analysis (Chain Analysis)
Specialized companies analyze the blockchain to link addresses and deanonymize users.
Analysis techniques:
1. Address clustering
- Pattern analysis: addresses used as inputs in the same transaction likely belong to the same owner
- Change address detection — identifying change outputs
- Temporal analysis — transactions at similar times
- Result: grouping thousands of addresses belonging to one user
2. Taint analysis
- Tracking coins from a known source
- If coins passed through your address — you're linked to the source
- Used for tracking stolen funds, darknet markets
3. UTXO analysis
- Bitcoin operates on the UTXO model (unspent transaction outputs)
- Each transaction creates a trail of UTXOs
- By analyzing UTXO combinations, ownership can be determined
4. Graph analysis
- Building transaction graphs
- Identifying hub addresses (exchanges, services)
- Determining fund flows between clusters
Companies specializing in this:
- Chainalysis — works with FBI, IRS, Europol
- CipherTrace — AML compliance for exchanges
- Elliptic — focus on criminal funds
- TRM Labs — risk assessment
These companies have databases with billions of clustered addresses linked to real identities.
Method 3: IP Address Tracking
When you send a transaction, your IP address can be linked to it.
How IP leaks occur:
- Full node — if you run your own node without Tor, your IP is visible to the network
- Light wallets (Electrum, SPV) — connect to other nodes, revealing your IP
- Web wallets — the server knows your IP with every login
- ISP logging — your provider sees connections to blockchain nodes
What can be learned from IP:
- Geolocation (city, sometimes neighborhood)
- ISP provider
- Connection to other online activities
- Temporal correlation (when you're online)
Method 4: Browser Fingerprinting and Cookies
Web wallets and DeFi applications can track you through your browser.
What's tracked:
- User Agent (browser, OS, versions)
- Screen resolution, fonts, plugins
- Canvas/WebGL fingerprinting
- Cookies and localStorage
- Wallet address when connecting MetaMask
Result: Even when changing wallets, you can be identified by your browser fingerprint.
Method 5: Social Engineering and OSINT
Open information on the internet can link you to crypto addresses.
Sources of leaks:
- Social media — posting "Just bought 1 BTC!" with an address
- Forums — signature with donation address on Bitcointalk
- GitHub — crypto addresses in developer profiles
- ENS domains — vitalik.eth linked to a public address
- NFT profiles — OpenSea shows all holdings
- Donation pages — "Support me" with a crypto address
Real case: In 2021, hackers tracked a wealthy Bitcoin holder through his Twitter posts where he mentioned his neighborhood. They conducted a physical attack ($5 wrench attack), stealing private keys under threat of violence.
Method 6: Timing Analysis
Analyzing transaction timing can reveal patterns.
What's analyzed:
- Transactions occur during 9-5 working hours EST? Probably from the US
- Always on weekend nights? Specific timezone
- Correlation with social media posts
- Sleep patterns (no transactions 00-08)
Risks of Lacking Privacy
Risk 1: Physical Attacks (Real-World Attacks)
If it's known that you hold significant cryptocurrency — you become a target.
Examples of attacks:
- $5 wrench attack — physical coercion to hand over keys
- Home invasion — break-in with the goal of theft
- Kidnapping — abduction for cryptocurrency ransom
- SIM-swapping after identification — knowing identity makes it easier
Statistics: According to Chainalysis, in 2022 there were 50+ documented cases of physical attacks on crypto holders with total damages >$100 million.
Risk 2: Financial Surveillance and Profiling
Your financial habits reveal your personal life.
What can be learned from transactions:
- Income level and wealth
- Purchasing habits
- Medical expenses (through pharmacy payments)
- Political views (campaign donations)
- Religious affiliation (donations)
- Sexual orientation (adult services)
- Gambling habits (casinos, betting)
This information can be used for:
- Targeted advertising
- Discrimination (employers, insurance)
- Blackmail
- Social engineering
Risk 3: Tax Issues
Full transaction transparency simplifies tax enforcement.
How tax authorities use blockchain:
- IRS purchases data from Chainalysis
- Automatic matching of addresses with tax returns
- Detection of unreported gains
- Penalties and criminal cases for tax evasion
Important: Privacy ≠ tax evasion. You can protect privacy and pay taxes legally.
Risk 4: Censorship and Fund Freezing
If authorities consider your transactions "suspicious":
- Tainted coins — coins that passed through mixers or darknet may be rejected by exchanges
- Account freezing — exchanges freeze accounts at authorities' request
- Sanctions lists — OFAC addresses are blocked
- Tornado Cash situation — using a mixer can be grounds for investigation
Risk 5: Corporate Surveillance
Companies collect blockchain data for commercial purposes:
- Targeted advertising based on holdings
- Selling databases of crypto users
- Credit scoring through on-chain history
- Employment screening (candidate verification)
Privacy Philosophy
"I have nothing to hide" — a dangerous position. Privacy isn't about hiding crimes, but about protecting the fundamental right to private life. You close the bathroom door not because you're committing a crime, but because it's a private space. Finances are equally private.
Privacy Protection Tools and Methods
Level 1: Basic Practices (For Everyone)
1. Use different addresses for different purposes
- Don't reuse addresses — each transaction = new receiving address
- HD wallets (BIP32/44) generate new addresses automatically
- Separation — separate wallets for trading, hodling, everyday spending
- Prevents clustering of all your funds
2. Always use a VPN
- Hides IP from blockchain nodes and web services
- Recommendations: Mullvad, ProtonVPN, IVPN (no-logs policy)
- Avoid: Free VPNs (they sell data)
- Enable before opening your wallet, not after
3. Tor for enhanced privacy
- Tor Browser — for accessing web wallets and DeFi
- Electrum through Tor — full privacy when using a light wallet
- Cons: Slower than VPN, some services block Tor exit nodes
4. Separate browser for cryptocurrencies
- Brave with telemetry disabled
- Firefox with privacy extensions (uBlock Origin, Privacy Badger)
- Disable JavaScript for sites where it's not needed
- Regularly clear cookies and localStorage
- Use containers (Firefox Multi-Account Containers)
5. Minimize connection to real identity
- Don't publish addresses on social media
- Don't brag about holdings and successful trades
- Use pseudonyms on forums and Telegram
- ENS domains — don't use your real name
Level 2: CoinJoin and Mixers
Technologies that break the link between input and output addresses.
What is CoinJoin
A protocol that allows multiple users to combine their transactions into one, making tracking difficult.
How it works:
- 10 users want to send 1 BTC each
- All coins are combined into one large transaction
- 10 outputs of 1 BTC each are created to new addresses
- Impossible to determine which input corresponds to which output
Popular CoinJoin implementations:
1. Wasabi Wallet
- Desktop wallet with built-in CoinJoin
- Uses Tor by default
- Minimum amount: 0.01 BTC
- Fee: ~0.3% to coordinator
- Pros: Proven technology, active development
- Cons: Requires time (mixing rounds)
2. Samourai Wallet
- Android wallet with Whirlpool CoinJoin
- Tor integration
- Ricochet — additional hops for distancing
- Pros: Mobility, additional privacy features
- Cons: Android only
3. JoinMarket
- Decentralized CoinJoin marketplace
- You can be a maker (provide liquidity) or taker
- Makers earn fees
- Pros: Full decentralization
- Cons: Complex for beginners
⚠️ CoinJoin Legality:
- Legal in most jurisdictions (US, EU)
- CoinJoin itself is not money laundering
- BUT some exchanges block "tainted" coins
- Consultation with a lawyer in your country is recommended
Centralized Mixers (NOT recommended)
Services like ChipMixer, Bitcoin Fog — a third party you trust with your coins.
Problems:
- Can steal your funds
- Can keep logs and share with authorities
- Many have been shut down by law enforcement
- Use may be considered money laundering
Tornado Cash (Ethereum)
Was the most popular mixer for ETH, but sanctioned by OFAC (US) in 2022.
Current status:
- Using Tornado Cash may lead to legal issues in the US
- Many exchanges block addresses that interacted with it
- NOT recommended to use without full understanding of risks

Level 3: Privacy Coins (Maximum Anonymity)
Cryptocurrencies designed specifically for privacy.
1. Monero (XMR)
Privacy technologies:
- Ring Signatures — your transaction is mixed with 15 others, impossible to determine the real sender
- Stealth Addresses — each transaction uses a one-time recipient address
- RingCT (Confidential Transactions) — transaction amounts are hidden
- Dandelion++ — hides sender's IP address
Result: Complete privacy by default. Impossible to see:
- Who sent
- Who received
- How much was sent
Advantages:
- ✅ Protocol-level privacy (no additional tools needed)
- ✅ Fungibility — all coins are equal, no "dirty" ones
- ✅ Proven technology (since 2014)
- ✅ Active development and community
Disadvantages:
- ❌ Delisted from many exchanges (regulatory pressure)
- ❌ Harder to buy legally
- ❌ Larger transaction size = higher fees
- ❌ Not supported by hardware wallets (most)
Monero Legality:
- Legal in most countries (including US, EU)
- BUT using it for criminal purposes = crime
- Some countries (South Korea, Japan) banned it on exchanges
2. Zcash (ZEC)
Technology:
- zk-SNARKs — zero-knowledge proofs for private transactions
- Shielded transactions — optional privacy
- Transparent transactions — like Bitcoin (for regulatory compliance)
Two types of addresses:
- t-addresses (transparent) — public, like Bitcoin
- z-addresses (shielded) — private
Problem: Only ~15% of transactions use shielded addresses. The rest are transparent.
3. Other privacy coins
- Dash — PrivateSend (CoinJoin), but optional
- Firo (formerly ZCoin) — Lelantus protocol
- Beam — Mimblewimble protocol
Why Monero is better: Privacy by default and mandatory. In Zcash and Dash, privacy is optional, which creates an anonymity set problem.
| Feature | Bitcoin | Monero | Zcash (shielded) |
|---|---|---|---|
| Sender hidden | ❌ | ✅ Ring Signatures | ✅ zk-SNARKs |
| Recipient hidden | ❌ | ✅ Stealth Addresses | ✅ zk-SNARKs |
| Amount hidden | ❌ | ✅ RingCT | ✅ zk-SNARKs |
| Privacy by default | ❌ | ✅ Always | ⚠️ Optional |
| Exchange availability | ✅ Everywhere | ⚠️ Limited | ✅ Many exchanges |
Level 4: Atomic Swaps and DEX
Exchanging cryptocurrencies without KYC and centralized intermediaries.
Atomic Swaps
- Peer-to-peer exchange between different blockchains
- BTC ↔ XMR without a third party
- Uses Hash Time-Locked Contracts (HTLC)
- Tools: unstoppableswap.net, comit.network
Decentralized Exchanges (DEX)
- Uniswap, SushiSwap, PancakeSwap — for Ethereum/BSC tokens
- Bisq — P2P exchange for BTC (no KYC)
- Thorchain — cross-chain swaps
- Incognito — privacy-focused DEX
Advantages:
- No KYC
- Non-custodial (you control the keys)
- Censorship-resistant
Disadvantages:
- Less liquidity
- Higher fees (gas fees)
- More complex for beginners
- Risk of smart contract vulnerabilities
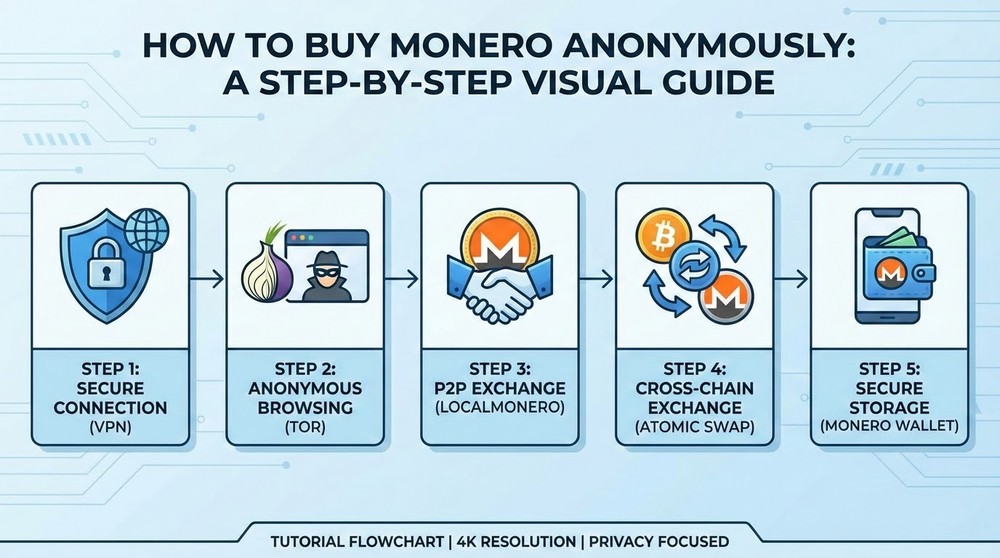
Practical Guide: How to Buy Monero Anonymously
Step-by-step instructions for maximum privacy.
Step 1: Preparation
- Install a VPN (Mullvad, ProtonVPN)
- Download Tor Browser
- Install Monero GUI wallet from the official site (through Tor)
- Create a new wallet — save the seed phrase
Step 2: Buying Without KYC
Option A: P2P platforms
- LocalMonero.co — Craigslist for Monero
- Choose a seller with good reputation
- Payment: cash, bank transfer, PayPal, gift cards
- Escrow protects against scams
- Fee: ~5-10% above market price
Option B: Bitcoin → Monero swap
- Buy BTC on no-KYC P2P (Bisq, HodlHodl, Robosats)
- Send BTC through CoinJoin (Wasabi Wallet)
- Exchange BTC → XMR through atomic swap (unstoppableswap.net)
- Receive XMR in your private wallet
Option C: Mining (most private)
- Monero can be mined on a regular CPU
- Install XMRig miner
- Connect to a pool (or solo)
- Payouts go directly to your address
- Completely anonymous, but requires time
Step 3: Usage
- Always through VPN/Tor
- Use subaddresses for different purposes
- Periodically churn (send to yourself) to refresh the ring
⚠️ Legal disclaimer: Anonymous purchasing is legal for privacy protection. Using it for tax evasion or criminal purposes is a crime.
Balancing Privacy and Compliance
You can protect privacy while remaining a law-abiding citizen.
Legal Ways to Maintain Privacy
1. Fund separation
- Public stack — funds with known source (salary, legal trading)
- Private stack — funds for everyday spending, hobbies, donations
- Pay taxes on the public stack
- Use privacy tools for the private stack
2. Proper reporting
- Declare all taxable events
- Use crypto tax software (Koinly, CoinTracker)
- Privacy ≠ hiding from the IRS
- You can use Monero and pay capital gains tax
3. Consultation with a crypto-savvy lawyer
- Laws vary by jurisdiction
- What's legal in one country may be problematic in another
- Professional consultation protects against mistakes
What's Legal and What's Not
✅ Legal:
- Using VPN and Tor
- Owning and using Monero (in most countries)
- CoinJoin for privacy protection
- Multiple wallets
- Atomic swaps without KYC
- Mining privacy coins
❌ Illegal:
- Tax evasion
- Money laundering of criminal funds
- Terrorism financing
- Purchasing illegal goods/services
- In some countries — using mixers (check local legislation)
⚠️ Gray area:
- Tornado Cash after OFAC sanctions
- Large sums without proof of origin
- Excessive use of privacy tools (may raise questions)
Conclusion: Privacy is a Right, Not a Crime
Protecting financial privacy is not an admission of guilt, but the exercise of a fundamental right to private life. In a world of total financial surveillance, privacy becomes a luxury available only to those willing to make the effort.
Core principles of a privacy-conscious approach:
1. Assume surveillance. Assume you're being watched. Act accordingly.
2. Defense in depth. Use multiple layers of protection, don't rely on one tool.
3. Privacy is a spectrum. Choose the level of privacy that matches your needs and risks.
4. Stay legal. Privacy is a legal right. Don't use it for illegal purposes.
Privacy technologies will continue to evolve. Regulators will continue to push. The balance between privacy and compliance is a complex task requiring constant attention and adaptation.
But one thing remains unchanged: your finances are your personal business. Protect them as carefully as you protect your home.
This was the final lesson of the course "Security: How Not to Lose Your Money." You've traveled from the basics of secure storage to advanced privacy techniques. Apply this knowledge, stay safe, and may your crypto assets remain under reliable protection.







