Module 6: What to Do If You've Been Hacked? (And Can You Recover Your Funds)
Introduction: The First Minutes After a Hack Are Critical
You open your wallet and see a zero balance. Your heart stops. Panic washes over you. This is one of the most terrifying moments for any crypto investor — realizing you've been hacked.
The statistics are brutal: according to Chainalysis, $3.7 billion in cryptocurrency was stolen in 2023. Less than 5% of that amount was recovered. Why so little? Because most victims either panic and take the wrong steps, or do nothing at all, believing the situation is hopeless.
But here's the good news: if you act quickly and smartly in the first minutes after discovering a hack, your chances of minimizing losses increase significantly. Sometimes you can even recover some of your funds.
Critical Fact: The first 15-30 minutes after a hack are the golden window of opportunity. During this time, hackers are still transferring funds, laundering through mixers, or withdrawing to exchanges. Taking the right actions during this period can save your money.

Signs of a Hack: How to Know If You've Been Compromised
A hack isn't always obvious. Sometimes the attack happens gradually, and early detection can prevent total loss of funds.
Clear Signs of an Active Hack
- Unexpected transactions — transfers you didn't make appear in your history
- Balance wiped out — all funds have disappeared
- Suspicious approvals — new permissions granted to unknown contracts
- NFTs missing — your collection transferred to another address
- Login attempts — emails about logins from unfamiliar devices/IPs
- Passwords not working — hacker changed access to your email or exchange
- Email compromised — you can't log into your email
Warning Signs Before a Hack
These signs indicate someone is trying to hack you or preparing an attack:
- Strange tokens in your wallet — unknown coins appeared with names like "Claim Reward"
- Dust attacks — micro-transactions to your address (goal — deanonymization)
- Phishing emails — suspicious messages from "exchange" or "support"
- 2FA attempts — receiving codes you didn't request
- Password change notifications — that you didn't initiate
- Suspicious social media activity — attempts to hack your Twitter/Telegram
- SIM card suddenly not working — possible SIM-swapping attack
How to Check Yourself Right Now
5-Minute Security Check:
- Check Revoke.cash or Etherscan Token Approvals
- Paste your address
- Review all active permissions
- Are there suspicious contracts with Unlimited Approve?
- Check transaction history
- Open Etherscan/BSCScan for your addresses
- Review the last 20 transactions
- Do you recognize all transactions?
- Check exchange accounts
- Security → Login History
- Are all logins from your devices?
- Any suspicious IP addresses?
- Check email security
- Gmail → Security → Recent Activity
- Any unfamiliar sessions?

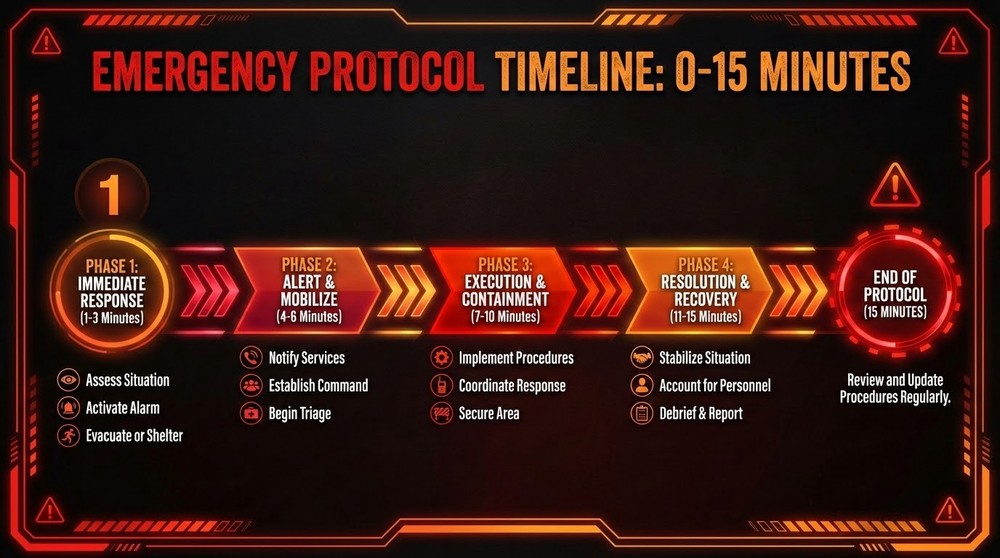
Emergency Response Protocol: The First 15 Minutes
Discovered a hack? Follow this protocol immediately. Every second counts.
Minute 1-2: Assess the Situation (DON'T Panic)
What to do:
- Take a deep breath — panic is the enemy of rational thinking
- Open Etherscan/BSCScan — check recent transactions
- Determine the scope — which wallets are compromised?
- Check if transactions are happening right now — is the attack active or complete?
What NOT to do:
- ❌ Don't close browser tabs (you'll need them for investigation)
- ❌ Don't try to transfer remaining funds chaotically
- ❌ Don't delete browser history
- ❌ Don't format your computer (you'll destroy evidence)
Minute 3-5: Stop Further Losses
For wallets (MetaMask, Trust Wallet):
- Create a new clean wallet on a different device
- Use your phone if computer was hacked
- Or computer if phone was hacked
- NEW seed phrase, no importing the old one
- Transfer remaining funds to the new address
- Start with the most valuable assets
- Use maximum gas for priority
- NFTs, tokens, everything that's left
- Revoke all approvals via Revoke.cash
- Access from a clean device
- Revoke ALL permissions for the compromised address
- Even if it costs gas — do it
For exchange accounts:
- Immediately change password (if you can still log in)
- Generate a random 20+ character password
- Use a different computer/phone
- Disable API keys
- If you have access — delete all APIs
- Hackers often use APIs to withdraw funds
- Freeze your account
- Binance: Security → Account Activity → Disable Account
- Coinbase: Settings → Security → Disable Account
- Better to freeze it yourself than lose everything
- Contact support
- Write to support chat: "Account compromised, freeze withdrawals"
- Provide account number, email
- Request withdrawal block
Minute 6-10: Protect Other Accounts
If one account is hacked, others may be at risk.
- Change email password
- If email is compromised — hacker gets access to everything
- Use a clean device
- Enable 2FA if you didn't have it
- Check forwarding rules in Gmail
- Settings → Forwarding and POP/IMAP
- Hackers often set up auto-forwarding of emails
- Delete suspicious rules
- Change passwords on all crypto services
- All exchanges, wallets, DeFi platforms
- Unique passwords for each
- Check other wallets
- If you used one computer for multiple wallets
- All may be compromised
Minute 11-15: Document the Attack
Gather evidence:
- Screenshots of all transactions on Etherscan
- Hacker addresses — where funds went
- Transaction hash of all suspicious transfers
- Timestamps of when it happened
- Browser history from recent days (possibly a phishing site)
- Login logs on exchanges
- Screenshots of emails with suspicious messages
Create a document with timeline:
Date/time of hack: [when discovered] Compromised addresses: [list] Stolen assets: [what and how much] Hacker addresses: [where funds went] How the hack occurred: [assumptions] Actions taken: [your steps]
Why Speed Is Critical
Most hackers follow scripts: steal → transfer to mixer → withdraw to exchange → cash out. The entire process takes 30-60 minutes. If you contact the exchange where funds went before the hacker cashes out — there's a chance to freeze them.
Tracking Stolen Funds: Blockchain Forensics
One advantage of blockchain is complete transaction transparency. Let's use this for tracking.
Basic Tracking via Etherscan
Step 1: Find the theft transaction
- Open Etherscan.io
- Paste your compromised address
- Find the suspicious transaction (Out)
- Click on the transaction hash
Step 2: Identify the hacker's address
- In transaction details, look at the "To" field
- This is the address where your funds went
- Copy this address
Step 3: Analyze the hacker's activity
- Paste the hacker's address into Etherscan
- Review all their transactions
- Where are they transferring funds next?
- Are there transfers to known exchanges?
What to look for:
- Transfers to exchanges — Binance, Coinbase addresses are visible by label on Etherscan
- Mixer usage — Tornado Cash, ChipMixer (complicates tracking)
- Bridges to other blockchains — BSC, Polygon, Arbitrum
- DEX interactions — token swaps
- Other victims — similar transaction patterns from different addresses
Advanced Tracking Tools
1. Blockchair.com
- Supports multiple blockchains
- Fund flow visualization
- Pattern search
2. Breadcrumbs.app
- Graphical transaction tracking
- Building connection graphs between addresses
- Cluster identification
3. Bloxy.info
- Ethereum transaction analytics
- Money flow diagrams
- Exchange and service identification
4. Wallet Explorer
- For Bitcoin
- Clustering addresses of the same owner
- Tracking through multiple transfers
5. Nansen.ai (paid, from $150/month)
- Professional on-chain analytics
- "Smart money" address identification
- Real-time alerts
- Worth the subscription for serious amounts
Identifying the Attack Type
Understanding the hack method helps with further actions.
Signs of different attack types:
| Attack Type | Blockchain Signs | Compromise Vector |
|---|---|---|
| Stolen seed phrase | All funds withdrawn at once, simple transfers | Phishing, malware, physical access |
| Malicious approve | Contract call, transferFrom function | Connecting to fake dApp |
| Exchange hack | Withdrawal via API, often to multiple addresses | Stolen credentials + 2FA bypass |
| SIM-swapping | Login from new device → withdrawal | SMS 2FA hacked through carrier |
| Clipboard hijacker | Transfer to address similar to yours | Malware replaces addresses |
![]()
Can You Recover Stolen Funds: Realistic Chances
The harsh truth: in most cases, stolen cryptocurrency cannot be recovered. But there are exceptions.
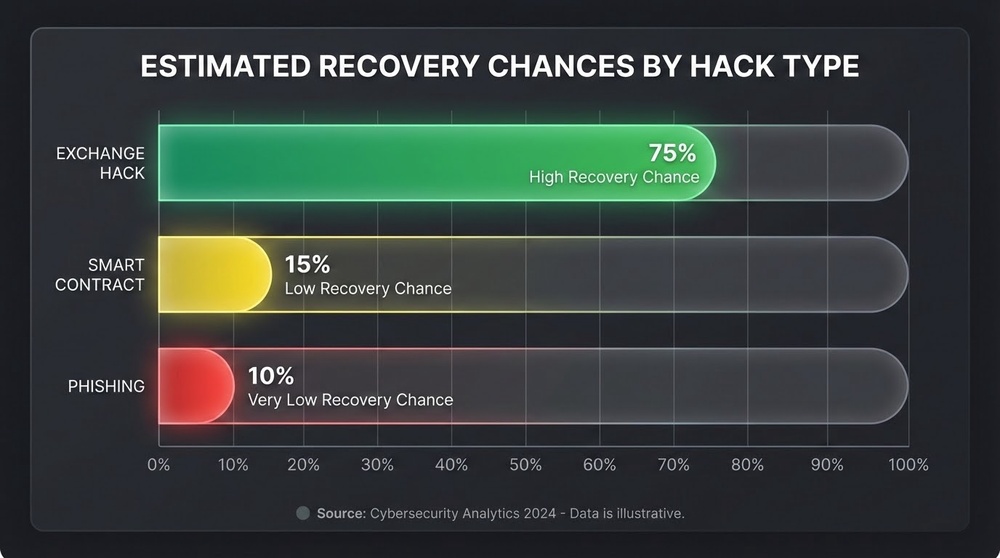
Scenario 1: Funds Still on Hacker's Address (30-50% chance)
Situation: Funds were stolen, but the hacker hasn't withdrawn/exchanged them yet.
What you can do:
- Front-running attack — if you know where the hacker will withdraw, you can try to send a transaction with higher gas before them (requires technical skills)
- Contact the hacker — sometimes on-chain messages with ransom offers help (5-10% of the amount)
- White hat hacker — hire a specialist to "hack back" (legality questionable)
Real case: In 2016, after The DAO hack, white hat hackers created a counter-attack and recovered some funds before the attackers could withdraw them.
Scenario 2: Funds on Centralized Exchange (10-20% chance)
Situation: You tracked funds to a deposit on Binance/Coinbase/Kraken.
What to do:
- Immediately contact the exchange
- Support ticket marked "Stolen Funds - Urgent"
- Provide transaction hash
- Hacker's deposit address on the exchange
- Proof of theft
- File a police report
- Exchanges respond better with official reports
- Even if local police aren't competent
- You need a case number for the exchange
- Provide maximum information
- Blockchain proof (Etherscan screenshots)
- Your personal data (for KYC)
- Proof of ownership of the stolen address
- Timeline of events
What the exchange can do:
- Freeze the hacker's account
- Block fund withdrawals
- Share data with law enforcement
- In rare cases — return funds to the victim
Reality: Exchanges are not obligated to return funds. If the hacker already passed KYC and withdrew — chances are minimal. But it's worth trying.
Scenario 3: Funds Went Through a Mixer (<5% chance)
Situation: The hacker used Tornado Cash or another mixer.
Reality: Tracking is virtually impossible. Mixers are designed specifically for anonymization.
What you can try:
- Hire a professional blockchain forensics company (Chainalysis, CipherTrace)
- Cost: from $5,000 per investigation
- Only makes sense for thefts >$100,000
- Even they don't guarantee results
Scenario 4: Smart Contract Vulnerability (40-70% chance)
Situation: The hack occurred through a vulnerability in a DeFi protocol or smart contract.
Examples:
- Reentrancy attack on contract
- Flash loan exploit
- Oracle manipulation
What can happen:
- Project team may conduct a hard fork (like after The DAO)
- Return funds to victims from reserve fund
- Negotiations with hacker (bounty for return)
- White hat rescue operation
Real recovery cases:
Poly Network (2021) — $611 million
- Hacker exploited cross-chain protocol
- Team reached out publicly
- Hacker returned all funds, received $500K bounty
- Called the hack a "learning moment for the industry"
Nomad Bridge (2022) — partial recovery
- Hacked for $190 million
- White hat hackers returned $36 million
- Team offered 10% bounty
- 19% of funds recovered
Scenario 5: Exchange Internal Hack (50-90% chance)
Situation: The exchange itself was hacked (not your fault).
Precedents:
- Mt.Gox (2014) — 850,000 BTC stolen, victims waiting for compensation 10+ years
- Binance (2019) — 7,000 BTC stolen, exchange compensated from insurance fund
- FTX (2022) — $8 billion disappeared, victims in legal proceedings
What it depends on:
- Exchange's insurance fund availability
- Jurisdiction and regulation
- Team's integrity
- Bankruptcy proceedings
Recovery Statistics: According to Chainalysis, only 2.2% of stolen funds are returned to victims. Most recoveries happen in DeFi protocol hacks (30-40% success) and when quickly contacting exchanges (10-15% success). Individual wallet hacks have <1% recovery chance.
Legal Actions: Where to Report
Even if recovery chances are low, proper legal documentation is important for taxes, insurance, and future investigations.
Step 1: Police Report
Where to report:
- Local police — first step, even if they're not competent
- Cyber police — specialized unit (if available in your country)
- FBI Internet Crime Complaint Center (IC3) — for US, accepts reports from everyone
- Action Fraud (UK) — for United Kingdom
- Europol — for European citizens
What to include in the report:
- Your personal information
- Date and time of hack
- Description of what happened
- Loss amount in cryptocurrency and fiat equivalent
- Blockchain evidence (addresses, transaction hash)
- Suspected method of hack
- Any contact with the hacker (if any)
Why this matters:
- Case number is required for exchanges
- For tax purposes (write off the loss)
- For insurance company (if insured)
- Creates official record of the incident
- May help in the future if hacker is found
Step 2: Specialized Agencies
Blockchain forensics companies:
1. Chainalysis
- Largest company in the field
- Works with FBI, Europol
- For individuals: from $5,000
- Makes sense for thefts >$100,000
2. CipherTrace
- Specializes in AML/compliance
- Tracking through mixers
- Works with exchanges and regulators
3. Elliptic
- Focus on crypto crimes
- Database of known hacker addresses
- Consultations from $3,000
4. CryptoRecovery.com and similar
- ⚠️ Caution: many are scams
- Promise "guaranteed" recovery for upfront payment
- Check reviews, don't pay in advance
- Legitimate ones work on "No recovery = No fee" basis
Step 3: Tax Deductions
In many jurisdictions, stolen cryptocurrency can be written off as a loss.
USA (IRS):
- Theft loss can be claimed on tax return
- Police report required
- Blockchain evidence
- Consultation with crypto CPA mandatory
UK (HMRC):
- Negligible value claim
- Reduces capital gains tax
- Action Fraud reference required
Europe:
- Varies by country
- Most allow writing off as a loss
- Consult with local tax advisor
Step 4: Public Disclosure
When it makes sense:
- Large amount (>$50,000)
- Want to warn the community
- Hope for help from blockchain detectives
- Put pressure on exchange/project
Where to post:
- Twitter — tag @zachxbt, @tayvano_ (known crypto investigators)
- Reddit r/CryptoCurrency — large community
- Bitcointalk — oldest forum
- Telegram groups — CryptoScamAlert and similar
What to include:
- Your story (briefly)
- Hacker addresses
- Transaction hashes
- Hack method (if known)
- Request for tracking help
⚠️ Risks:
- Public information can be used against you
- Attracts attention of other scammers
- "Recovery scammers" will offer help for money
Prevention: How to Avoid Getting Hacked
The best "recovery" is prevention. Let's review a security checklist that protects against 99% of attacks.
Critical Measures (Mandatory for Everyone)
- Never enter your seed phrase anywhere except recovery on your own device
- Use a hardware wallet for amounts >$5,000
- Enable TOTP 2FA (not SMS) on all exchanges and email
- Check URLs three times before entering data
- Regularly revoke approvals via Revoke.cash (monthly)
- Antivirus + regular scans of your system
- Separate browser/profile only for cryptocurrency
- Don't click links in Twitter/Telegram/Discord DMs
- Use a password manager with unique passwords
- Store backup copies of seed phrases offline
Advanced Measures (For Large Portfolios)
- Multisig wallet for amounts >$100,000
- YubiKey hardware keys for exchanges
- Dedicated computer only for cryptocurrency (air-gapped for cold storage)
- VPN always on when working with crypto
- Address whitelisting for withdrawals on exchanges
- 24-48 hour withdrawal delay (option on some exchanges)
- Regular security audits (professional, annually)
- Legal structuring (trusts, will with crypto instructions)
- Crypto insurance (if available in your jurisdiction)
Monitoring and Alerts
Set up notifications:
- Etherscan Email Alerts — notifications for every transaction on your address
- Whale Alert — for large wallets
- Zerion/Zapper notifications — portfolio changes
- Exchange alerts — logins from new devices, API activity
- Google Account Activity — suspicious email logins
Psychological Support: How to Cope with Loss
A hack and loss of funds is a traumatic experience. It's important to handle it properly.
Stages of Acceptance (Kübler-Ross Model)
1. Denial — "This can't be true, must be a mistake"
2. Anger — "How could this happen! Why me!"
3. Bargaining — "If I find the hacker, I'll get at least some back..."
4. Depression — "I lost everything, it's over"
5. Acceptance — "It happened, I'll learn from it and move forward"
Healthy ways to cope:
- Talk to loved ones — don't keep it inside
- See a therapist — for major losses
- Join support groups — r/CryptoScamVictims, forums
- Document your experience — write what happened (catharsis)
- Focus on what you can control — what can you improve in the future
- Don't make impulsive decisions — don't try to "win back" with risky investments
What NOT to do:
- ❌ Don't blame only yourself — hackers are professionals
- ❌ Don't hide it from loved ones — this worsens stress
- ❌ Don't try to hack back using illegal methods
- ❌ Don't give up on crypto forever — learn from it
- ❌ Don't neglect physical health (sleep, food, exercise)
Remember: Losing money is not losing yourself. Many successful crypto investors have gone through hacks and came back stronger. Andreas Antonopoulos, Vitalik Buterin, many well-known industry figures have had negative experiences. The key is to learn the lesson and strengthen security.
Real Recovery Stories
Story 1: Quick Reaction Saved $180,000
A user noticed the hack within 5 minutes thanks to Etherscan email alert. Immediately contacted Binance (where the hacker deposited). Provided evidence. Binance froze the hacker's account. 80% of funds returned within 2 weeks.
Lesson: Set up alerts. Speed is everything.
Story 2: Community Helped Identify the Hacker
Victim posted hack details on X.com for $75,000. Blockchain detective @zachxbt tracked funds through a mixer to a known hacker group. Information passed to FBI. A year later, the group was arrested, victim received 60% compensation.
Lesson: Public disclosure sometimes works.
Story 3: $2 Million Loss Without Recovery
Investor stored everything in one hot wallet. Malware stole the seed phrase. Hacker used Tornado Cash. Funds were not recovered.
Lesson: Storage diversification + cold wallets for large amounts.
Conclusion: A Hack Is Not a Sentence, It's a Lesson
If you're reading this lesson after a hack — accept our sincere condolences. It's a difficult experience. But remember: in cryptocurrency, you have complete control over your money, and that means complete responsibility for security.
Follow the protocol from this lesson. Even if you can't recover the funds, proper documentation and legal filing are important for taxes and the future.
For those reading preventively: do everything to never find yourself in a hack situation. Invest in security — hardware wallets, 2FA, education. It's always cheaper than losing funds.
In the next lesson, we'll study the DYOR (Do Your Own Research) principle — how to independently verify information and make informed decisions in the crypto industry.







